A tool created by developer Felix Krause reveals hidden JavaScript injections through in-app browsers.
In-app browsers offer a convenient way for developers to let users browse specific websites without leaving their apps. However, they can be used to invade users’ privacy.
A JavaScript injection can be used via an in-app browser to collect data about users including their taps on a webpage, keyboard inputs, and more.
Armed with this data, a “digital fingerprint” can be created of a specific individual which can be used for targeted advertising.
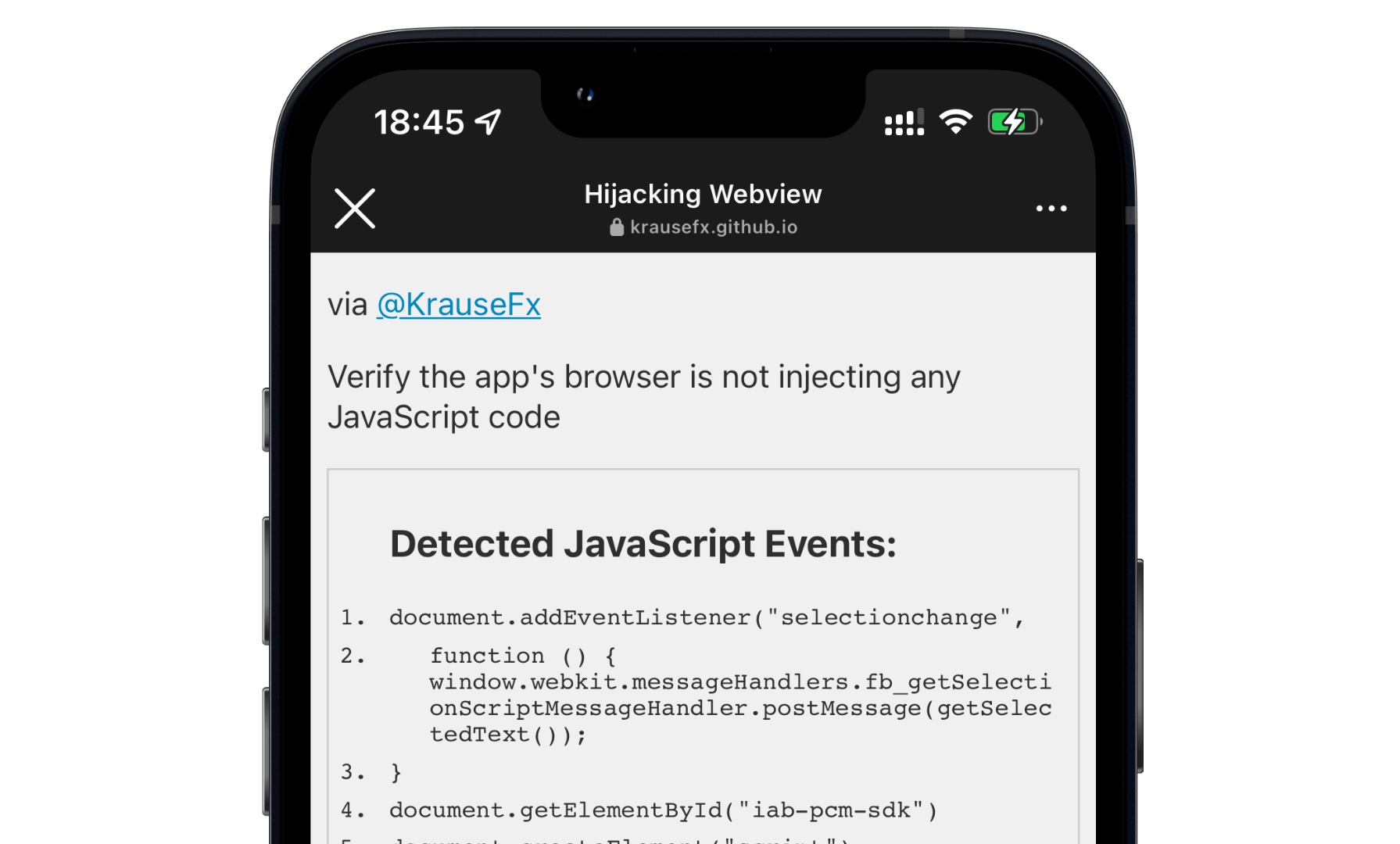
Krause created a tool called InAppBrowser that can generate a report about the JavaScript commands that a developer is running through an in-app browser.
To use the tool, you only have to open the app you wish to analyse and use the in-app browser to open the URL “https://InAppBrowser.com”.
Krause has already tested some popular apps using his tool, including TikTok and Instagram.
TikTok was found to monitor all keyboard inputs and screen taps when using its in-app browser. Instagram, meanwhile, was able to detect all text selections on websites.
In a disclaimer about his tool’s limitations, Krause wrote:
“This tool works by overriding the most common JavaScript functions, however the host app may still inject other commands.
As of iOS 14.3, Apple introduced a new way of running JavaScript code in an ‘Isolated World’, making it impossible for a website to verify what code is being executed.
Also, this tool cannot detect other app tracking that may occur, such as custom gesture recognition, screenshot detection, or tracking of web request events.”
Not all apps that inject JavaScript code are doing so for malicious purposes, but InAppBrowser may help to uncover those that are doing so without good reason and dissuade others.

Want to learn more about cybersecurity and the cloud from industry leaders? Check out Cyber Security & Cloud Expo taking place in Amsterdam, California, and London. The event is co-located with the Blockchain Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.






