
GitHub has launched its secret scanning tool for private repositories alongside a new security overview dashboard.
The world’s largest repo host first unveiled the fraud-preventing secret scanning feature in May last year as part of GitHub Advanced Security—a package of features that includes code scanning, secret scanning, and dependency reviews.
Secret scanning has been in beta until today. Since it was first announced, GitHub says it has:
- Expanded secret scanning’s pattern coverage to cover tokens from more than 35 partners
- Added an API and webhooks for secret scanning alerts
- Started sending notifications to commit authors (as well as admins) when they commit secrets
GitHub says the feature has already helped organisations discover and revoke over 5,000 exposed secrets.
As part of today’s announcement, GitHub is also launching a new “security overview” which aims to provide a single, high-level overview of security risks a GitHub organisation is exposed to.
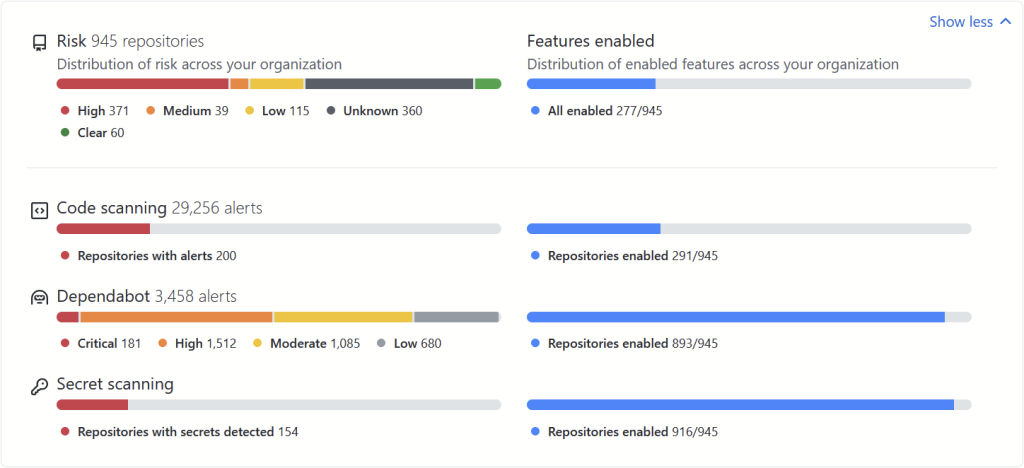
The dashboard shows any security risks detected by code scanning, Dependabot, and secret scanning. Filters enable developers to focus on specific repos such as public ones deemed high-risk.
Find more about security overview and secret scanning in GitHub Docs.
(Photo by Richy Great on Unsplash)
Interested in hearing industry leaders discuss subjects like this? Attend the co-located 5G Expo, IoT Tech Expo, Blockchain Expo, AI & Big Data Expo, and Cyber Security & Cloud Expo World Series with upcoming events in Silicon Valley, London, and Amsterdam.






